# Software Security
TIP
Security vs. Convenience: The Ultimate Trade-Off? A Balancing Act
# HTTPS
Data is encrypted in transit in both directions: going to and coming from the origin server
avoid man in middle attack
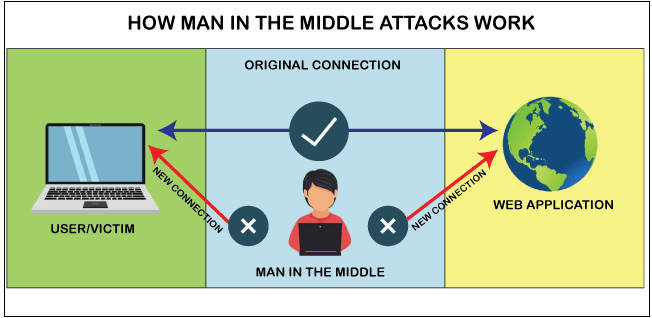
How
- Buy SSL then set up on your server
- Use let's encrypt (opens new window) to generate one SSL for free
- Free SSL from cloudflare (opens new window)
# Limit rating
Limit rating allows us to control the rate at which user requests are processed by our server. Avoid:
- Brute force attack
- DoS & DDoS attack
- Web scraping
How
- Setup at DNS Service like cloudflare (opens new window)
- Setup at Application . E.g throttler of NestJs (opens new window). Don't forget storage for this feature must be fast 👿
Read more: Rate-limiting strategies and techniques (opens new window)
# Information hiding
Attacker can use tool to scan vulnerability list (opens new window) that's why hide information is important thing in to-do list
- Hide detail of error response, turn off debug mode on production
- Hide technologies Backend languages by removing redundant header attributes
- Hide frontend libraries by using obfustace or uglify tool, remove meta information
- Hide sensitive route , rename default links of system. E.g in wordpress
/wp-adminto/no-duty-to-waive-entry😎 - ...
# Cache Miss Attack Prevention
attacker purposely tries to cache miss, the attacker can overload your application and database.
Example:
Example.com?cachemiss1
Example.com?cachemiss2
Example.com?cachemiss3
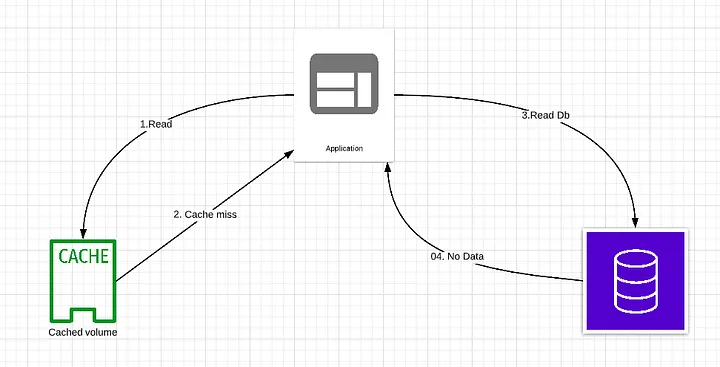
Solution
- Whitelist the allowed parameters, strip invalid parameters
- Set a short TTL for keys with null value
- Using Bloom filter. A Bloom filter is a data structure that can rapidly tell us whether an element is present in a set or not. If the key exists, the request first goes to the cache and then queries the database if needed. If the key doesn't exist in the data set, it means the key doesn’t exist in the cache/database. In this case, the query will not hit the cache or database layer.
Read more:
- cache miss attack (opens new window)
- Bloom Filters: Tại sao các mạng blockchain lại thường sử dụng nó (opens new window)
# Payment Security
... TBD
# Authentication
# Store Password Safely
WARNING
- Never store raw/plain password
- Storing password hashes directly is not sufficient because it is pruned to precomputation attacks, such as rainbow tables (opens new window).
To mitigate precomputation attacks, we salt the passwords.
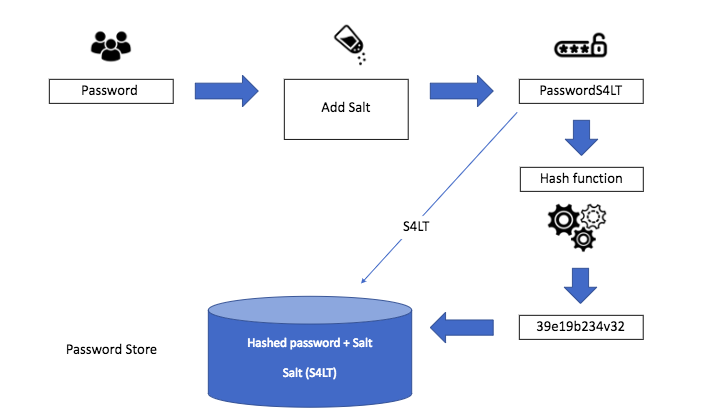
Sending raw password in payload from browser on HTTP protocol is not a good idea. Hash password before send to server is better. Server has no chance to know what is the raw password of user.
# Two/Multi Factor Authentication (2FA / MFA)
strengthens access security by requiring two methods to verify identity
How
- Hardware Tokens (opens new window) for 2FA
- SMS Text-Message and Voice-based
- Software Tokens for 2FA. E.g: Time-based one-time password (TOTP) (opens new window), Google Authenticator (opens new window), ...
- Push notification . E.g send request to other devices of owner
- Biometric. E.g: fingerprint, facial recognition, ...
# Authorization aka Access Control
Access control is the application of constraints on who can perform attempted actions or access resources that they have requested. Broken access controls are a commonly encountered and often critical security vulnerability.
Design and management of access controls is a complex and dynamic problem that applies business, organizational, and legal constraints to a technical implementation. Access control design decisions have to be made by humans, not technology, and the potential for errors is high.
Solution
- Checking permission 👿 more testing 👿
- Avoid Misconfiguration
- Unless a resource is intended to be publicly accessible, deny access by default
- Wherever possible, use a single application-wide mechanism for enforcing access controls.
- At the code level, make it mandatory for developers to declare the access that is allowed for each resource, and deny access by default.
- Thoroughly audit and test access controls to ensure they are working as designed.
Read more Access control vulnerabilities and privilege escalation (opens new window)
# Insecure direct object references (IDOR) Prevention
IDOR is a type of access control vulnerability that arises when an application uses user-supplied input to access objects directly.
Solution
- Apply rating limits
- Avoid using
AUTO_INCREMENTfor IDs that allows guessing other Ids easily => Attacker can fetch all of records if there is an accessible API - Use UUID => allow you to merge rows from different databases or distribute databases across servers
- Use flake-idgen (opens new window) . The Flake ID is made up of:
timestamp,datacenter,workerandcounterconflict-free ids in a distributed environment.
Read more: MySQL UUID Smackdown: UUID vs. INT for Primary Key (opens new window)
# Cross Site Scripting (XSS) Prevention
3 types of XSS
- Reflected XSS (aka Non-Persistent) through POST form
- Stored XSS (aka Persistent) through query string
- DOM Based XSS (new)
# Cookie Attributes
httpOnly=> prevents client-side scripts from accessing data
# Web Application Firewall (WAF)
How do I create an AWS WAF rule to prevent SQLi and XSS? (opens new window)
# Content Security Policy (CSP)
CSP is an added layer of security that helps to detect and mitigate certain types of attacks, including Cross-Site Scripting (XSS) and data injection attacks.
<meta
http-equiv="Content-Security-Policy"
content="default-src 'self'; img-src https://*; child-src 'none';" />
- Restricting Remote Scripts
- Restricting Unsafe JavaScript
- Restricting Form submissions
- Restricting Objects => won't be possible to inject malicious flash/Java/other legacy executables on the page.
Common use cases
- A web site administrator wants all content to come from the site's own origin (this excludes subdomains.)
Content-Security-Policy: default-src 'self'
- A web site administrator wants to allow content from a trusted domain and all its subdomains (it doesn't have to be the same domain that the CSP is set on.)
Content-Security-Policy: default-src 'self' example.com *.example.com
- A web site administrator wants to allow users of a web application to include images from any origin in their own content, but to restrict audio or video media to trusted providers, and all scripts only to a specific server that hosts trusted code.
Content-Security-Policy: default-src 'self'; img-src *; media-src example.org example.net; script-src userscripts.example.com
- A web site administrator for an online banking site wants to ensure that all its content is loaded using TLS, in order to prevent attackers from eavesdropping on requests.
Content-Security-Policy: default-src https://onlinebanking.example.com
- A web site administrator of a web mail site wants to allow HTML in email, as well as images loaded from anywhere, but not JavaScript or other potentially dangerous content.
Content-Security-Policy: default-src 'self' *.example.com; img-src *
Read more:
# Validate / sanitize input from user
- Cleaning Content
- detect and remove invalid HTML tags. E.g:
<script />, or<iframe /> - detect and remove invalid attributes. E.g:
<img onload="attacking script" >
- detect and remove invalid HTML tags. E.g:
# Encoding, be careful output
Using framework
React
const markup = { __html: '<p>some raw html</p>' };
return <div dangerouslySetInnerHTML={markup} />;
Vue
<p>Using v-html directive: <span v-html="rawHtml"></span></p>
CSS Contexts
URL Contexts
Dangerous Contexts
<script>Directly in a script</script>
<!-- Inside an HTML comment -->
<style>Directly in CSS</style>
<div ToDefineAnAttribute=test />
<ToDefineATag href="/test" />
Other areas to be careful of include:
- Callback functions
- Where URLs are handled in code such as this CSS { background-url : “javascript:alert(xss)”; }
- All JavaScript event handlers (
onclick(),onerror(),onmouseover()). - Unsafe JS functions like
eval(),setInterval(),setTimeout()
Don't place variables into dangerous contexts as even with output encoding, it will not prevent an XSS attack fully.
Source: Cross Site Scripting Prevention Cheat Sheet (opens new window)
# SQL Injection (SQLi) Prevention
Recently, many libraries, frameworks support automatically escapes all variables / parameters by default. But sometimes, you must use a raw query Sql to execute... Read the document carefully.
mysqli of PHP
Prisma of Nodejs
Read more excess-xss (opens new window)
# Cross-Site Request Forgery (CSRF) Prevention
...
# More solution
- If using a wordpress, install plugin iThemes Security (opens new window)
- 10 Ways to Prevent Phishing Attacks (opens new window)
- OWASP Top Ten (opens new window)