# Authentication
TIP
Authentication is the act of proving an assertion, such as the identity of a computer system user.
# Top Mechanisms
# Most used
- SSH Keys: Cryptographic keys are used to access remote systems and servers securely
- OAuth Tokens: Tokens that provide limited access to user data on third-party applications
- SSL Certificates: Digital certificates ensure secure and encrypted communication between servers and clients
- Credentials: User authentication information is used to verify and grant access to various systems and services
# REST API

- Basic Authentication
- Token Authentication
- OAuth Authentication
- API Key Authentication
# API key vs Token

| Feature | Api keys | Tokens |
|---|---|---|
| Purpose | Application identification | User authentication |
| Lifespan | Long-lived, static | Short-lived, dynamic |
| Permissions | Fixed set | User-specific, variable |
| User context | No user information | Contains user data |
| Security | Less secure if compromised. Regular Rotation helps. | More secure, limited lifespan |
# Signal in Request
There is always a sign in HTTP request to be used for Authenication
- URL:
/post/create?api_key=my_key - Cookie: SESSION_ID=CLIENT_TOKEN
- Authorization Header:
Authorization: my_token - Custom Header:
Authorization: my_token - Body:
content=...&token=my_token
# Basic Authentication
TIP
Basic Authentication is a method for an HTTP user agent (e.g., a web browser) to provide a username and password when making a request.
Authorization: Basic <credentials>
- The user’s username and password are combined with a
:(colon) . - The resulting string is base64 encoded.
Pros
- easy, most of browsers & servers support
- easy to integrate with other methods
Cons
- Username/password are easy to be leaked because of embeded in every request
- No feature call logout. Except remove browsing history
- No friendly UI
# Session-based Authentication
Sometimes, it was also called cookie-based authentication.
TIP
Session Authentication is a small file, most likely in JSON format, that stores information about the user, such as a unique ID, time of login and expirations, and so on. It is generated and stored on the server so that the server can keep track of the user requests.
The user receives some of these details, especially the ID, as cookies that will be sent with every new request, so that the server can recognize the ID and authorize the user’s requests.
Used for monolith system, small website, PHP websites by default, ...
Pros
- Inforamtion hiding. Session Id is randomly generated without user infor
- Small size to transfer
- No need to handle at client too much, because all browsers support cookie by default behaviour
- Fully-controlled session. E.g: time to expire for login, force logout, ...
Cons
- take up a lot of storage in Server
- difficult to scale out because by default
- Should configure Session storage to a global storage, all app instances
- Or should remain the connection of
session idand the servingapp instance
- depends on domain
CSRFattacking
# Token-based Authentication
TIP
A token is an authorization file that cannot be tampered with. It is generated by the server using a secret key, sent to and stored by the user in their local storage. Like in the case of cookies, the user sends this token to the server with every new request, so that the server can verify its signature and authorize the requests.
Used for system Web API, Distributed system, micro-services, system has multi-platform mobile, IoT, server,... or UI / API seperation
# Session-based vs Token-based Authentication
| Session-based Auth | Token-based Auth |
|---|---|
| Server stateful, take up a lot of storage in Server | Server stateless, token has attribute self-contained |
| SessionId at client has no user information | Token contains user information |
| Small size to transfer | Bigger size |
| Use only on 1 url domain | Token can be sent to many url domains |
| No need to handle at client too much, browsers support cookie by default | More complicated handling at client. E.g Store token, refresh token, attach token to each request, ... |
Be careful about CSRF | Prevent CSRF |
| Use for browsers | Not only browser-to-server but for server-to-server |
| Server is difficult to scale out | Easy to scale out |
Criteria Comparision
| Criteria | Session-based Auth | Token-based Auth |
|---|---|---|
| Which side stores the authentication details | Server | Client (Browser) |
| What Client sends to Server to have their requests authorized | A cookie | Token |
| What Server does to authorize users’ requests | Look up sesssionId requested by client on storage | Decrypting the user’s token and verifying its signature |
| Kind of attacks the method may suffer | Man-in-middle, Cross-site request forgery (CSRF) | Man-in-middle, Token steal, breaches of the secret key |
| Force logout feature by admin | Fully-controlled session | Implemented by coding, make blocklist token, make server becomes stateful |
See more: Session vs Token Based Authentication (opens new window)
# Hash based Message Authentication Code (HMAC)
TIP
Hash-based message authentication code (or HMAC) is a cryptographic authentication technique that uses a hash function and a secret key.
With HMAC, you can achieve authentication and verify that data is correct and authentic with shared secrets
Two parties want to communicate, but they want to ensure that the contents of their connection remain private. They also distrust the internet, and they need a way to verify that the packets they receive haven't been tampered with. HMAC is a valid solution.
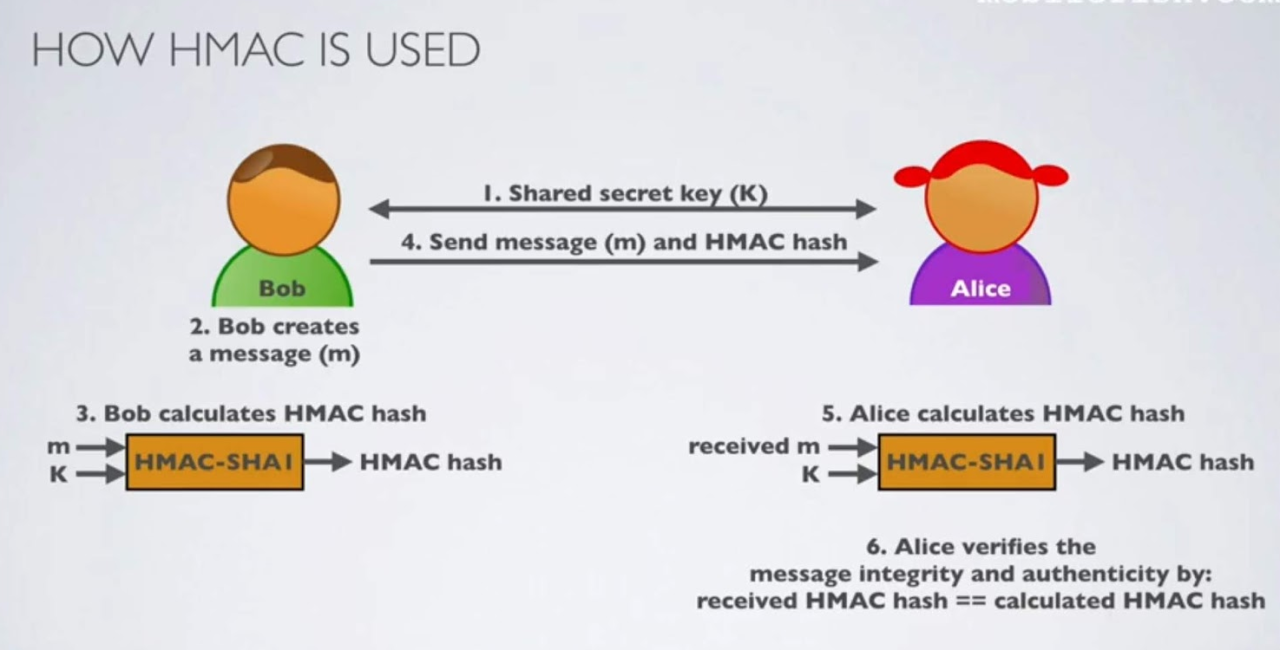
How it works
HMACs provides client and server with a
shared private keythat is known only to them.The client makes a unique hash (HMAC) for every request. When the client requests the server, it hashes the requested data with a private key and sends it as a part of the request. Both the message and key are hashed in separate steps making it secure.
When the server receives the request, it makes its own HMAC. Both the HMACS are compared and if both are equal, the client is considered legitimate.
The formula for HMAC:
HMAC = hashFunc(secret key + message)
Example PUT method Amazon S3 documentation (opens new window)
"Authorization: AWS " + AWSAccessKeyId + ":" + base64(hmac-sha1(VERB + "\n"
+ CONTENT-MD5 + "\n"
+ CONTENT-TYPE + "\n"
+ DATE + "\n"
+ CanonicalizedAmzHeaders + "\n"
+ CanonicalizedResource))
PUT /quotes/nelson HTTP/1.0
Authorization: AWS 44CF9590006BF252F707:jZNOcbfWmD/A/f3hSvVzXZjM2HU=
Content-Md5: c8fdb181845a4ca6b8fec737b3581d76
Content-Type: text/html
Date: Thu, 17 Nov 2005 18:49:58 GMT
X-Amz-Meta-Author: foo@bar.com
X-Amz-Magic: abracadabra
Usage scenarios
- Verification of e-mail address during activation or creation of an account.
- Authentication of form data that is sent to the client browser and then submitted back.
- HMACs can be used for Internet of things (IoT) due to less cost.
- Whenever there is a need to reset the password, a link that can be used once is sent without adding a server state.
- It can take a message of any length and convert it into a fixed-length message digest. That is even if you got a long message, the message digest will be small and thus permits maximizing bandwidth.
See more:
# OAuth 2.0

OAuth 2.0 (Open Authorization) Explained With Simple Terms.
OAuth 2.0 is a powerful and secure framework that allows different applications to securely interact with each other on behalf of users without sharing sensitive credentials.
The entities involved in OAuth are the User, the Server, and the Identity Provider (IDP).
What Can an OAuth Token Do?
When you use OAuth, you get an OAuth token that represents your identity and permissions. This token can do a few important things:
Single Sign-On (SSO): With an OAuth token, you can log into multiple services or apps using just one login, making life easier and safer.
Authorization Across Systems: The OAuth token allows you to share your authorization or access rights across various systems, so you don't have to log in separately everywhere.
Accessing User Profile: Apps with an OAuth token can access certain parts of your user profile that you allow, but they won't see everything.
Remember, OAuth 2.0 is all about keeping you and your data safe while making your online experiences seamless and hassle-free across different applications and services.
# SSO

# MFA